The on-board Intel NICs support booting from an iSCSI target LUN, however they are not flashed to do so; rather they are ready for PXE booting.
The iSCSI configuration in the BIOS settings does not apply to iSCSI on these NICs. I’m not sure but maybe if you’re doing iSCSI via the MLOMs or 10GB cards those BIOS settings might come into play.
The first thing to do is re-flash the NICs to boot iSCSI. Using https://community.cisco.com/t5/data-center-and-cloud-knowledge-base/how-to-iscsi-boot-with-intel-i350-adapters-on-ucs-servers/ta-p/3123679 as the basis:
Download ucs-cxxx-utils-efi.3.1.3.iso from the Cisco website. It’s found under your specific C-series server. For example:
- Downloads Home
- Servers – Unified Computing
- UCS C-Series Rack-Mount Standalone Server Software
- UCS C220 M4 Rack Server Software
- Unified Computing System (UCS) Utilities
- EFI 3.1(3)
Mount the ISO on your local machine (not the server) and copy the file /Network/Intel/BootUtil/BootUtil-v1.6.57.0.zip to a folder somewhere. Extract it. Copy the file BootUtil-v1.6.57.0/BOOTUTIL64E.EFI to a USB stick (FAT or FAT32 formatted – maybe even ExFAT).
Now boot the UCS server into the EFI shell. Insert the USB and navigate to the USB: The map command is your friend. On my system the USB was automatically mapped to fs0.
You need to choose which NIC will perform the iSCSI mount. The thread above mentions people having issues with the iSCSI breaking once ESXi boots and steals the port for management. I didn’t have this issue, although I was using port 2 (only). One oddity is the IP address that the NIC is given via DHCP changes once ESXi boots. This isn’t an issue – but the initial iSCSI session drops and gives way to a second session when ESXi get an IP.
Anyhoo, now that you’ve booted EFI and mounted the USB, and chosen which NIC (or both) to configure for iSCSI, you need to play with BOOTUTIL64E.EFI:
Without any options you’ll get the state of both NICs:
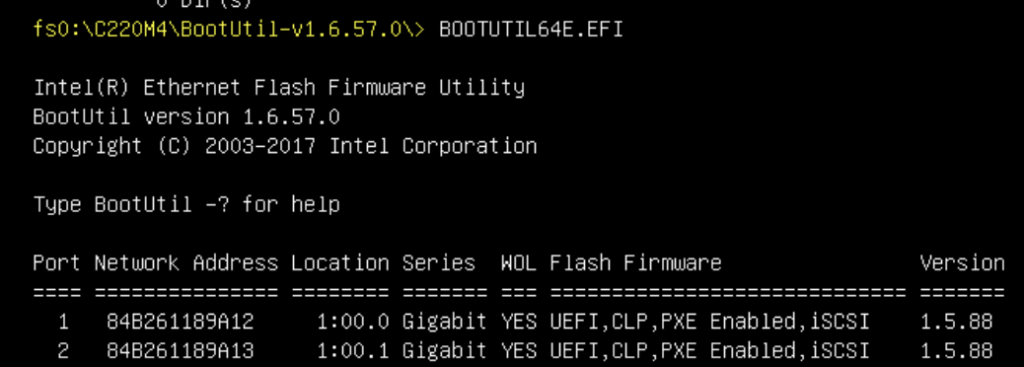
The example configures port one (NIC 1) as the primary iSCSI boot NIC:
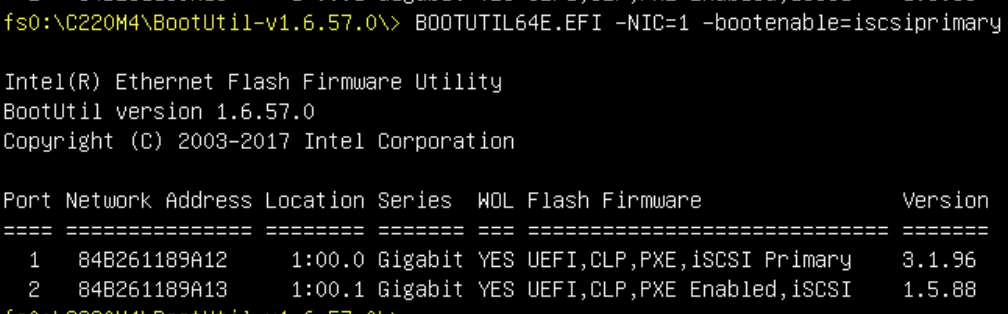
As I mentioned I ended up using port 2 so the following examples will show that. Once that’s done, unplug the USB stick and reboot. This time during the boot process you’ll get an opportunity to hit Ctrl-D to configure iSCSI on the NIC. When you hit Ctrl-D you’ll be presented with the Intel iSCSI Remote Boot utility:
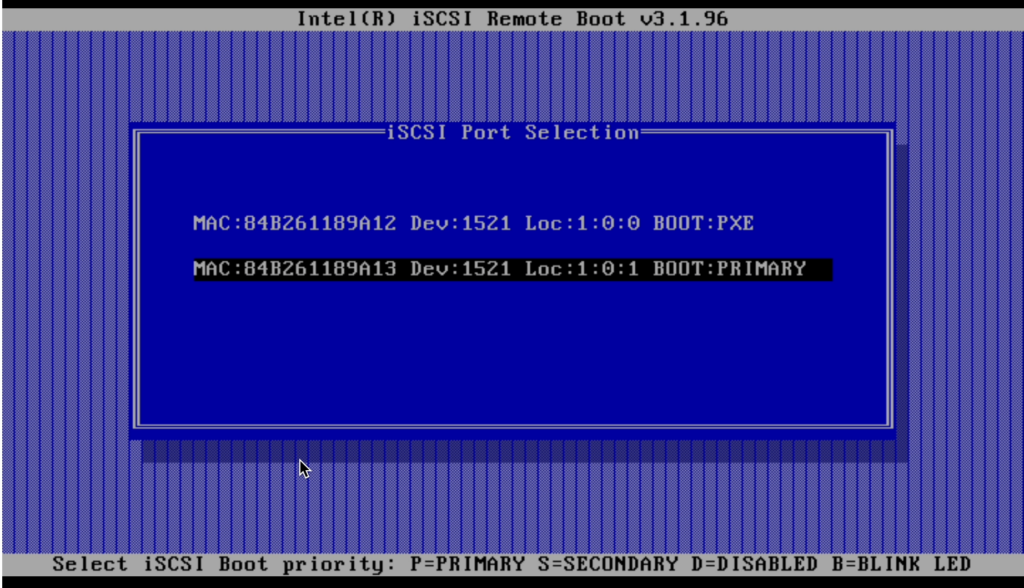
Choose the primary NIC (or both, one after the other, if you have configured primary and secondary NICs). In the next window you’ll choose “iSCSI Boot Configuration” to configure IP and iSCSI initiator and target details. My setup used DHCP for the IP configuration. Since I also use authentication I also needed to configure the “iSCSI CHAP Configuration” page.
Save changes and exit, and you see the initiator attempt to connect to the iSCSI target.
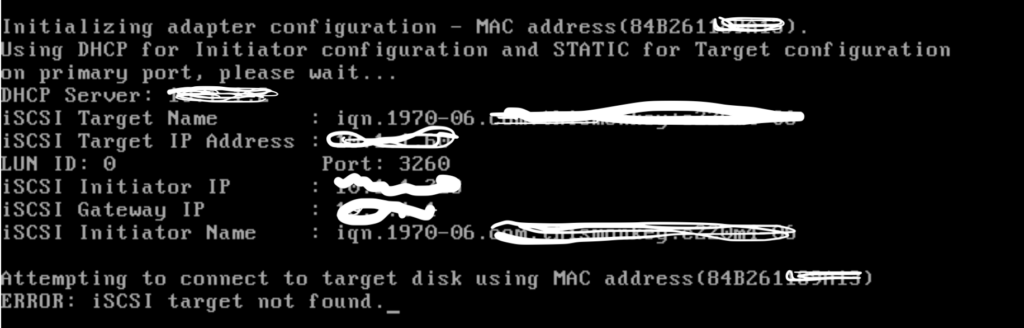
As you can see I initially configured the incorrect target name. You get very little time to see such messages and the boot processes continues. Some screen recording of the KVM session and looking at the iSCSI target logs confirmed my initial mistake. The following log entry on the target confirms my initial misconfiguration on the iSCSI initiator:
ctld[12943]: a.b.c.d (iqn.1970-06.initiator): requested target "iqn.1970-06.target" not found
Once fixed, I see no errors in the ctld logs and I see a session in ctladm islist:
23 ip-addr-1 iqn.1970-06.initiator iqn.1970-06.target
And once ESXi boots (and the IP changes):
26 ip-addr-2 iqn.1970-06.initiator iqn.1970-06.target
When installing ESXi you’ll see a Remote disk (the iSCSI disk) on which you can install it.
I use NFS to mount the ESXi installer ISO via the CIMC with:
map-nfs esxi-installer <nfs-server>:</path/to/ISO/directory/> VMware-VMvisor-Installer-7.0U2-17630552.x86_64.iso ro